2 years of Securing Laravel / Laravel Security In Depth!
Thank you for subscribing and supporting Securing Laravel these past 2 years!

Greetings, my friends!
We just passed the 2 year anniversary of Securing Laravel! 🎉 🎂
I sent out the first email to Laravel Security In Depth (as it was called then) on the 31st August 2021 during Laracon Online, unsure how popular this crazy idea of mine would be. Substack was still fairly new, and as far as I’d seen, no one else in the Laravel community was trying a paid mailing list. So I was unsure how well it’d be received, or if anyone would sign up. But sign up they did and now, 2 years later, we’re up at 2,521 total subscribers1!
I am incredibly proud of this number and everything I’ve achieved through Securing Laravel. All of the support I have received has been incredible, and I have loved writing these emails to you each week.
Thank you all so much for supporting, sharing, and subscribing to Securing Laravel! It means so much to me, and keeps me writing each week. Also, a special thank you to my paid subscribers who support my work financially. As a self-employed security consultant, having financial support for non-client things is incredibly valuable and it means so much.
As I did last year, I want to take a week off from my Security Tips and In Depth articles to reflect on the past year. So let’s take a look at the past year, what I posted, what worked, what didn’t, and what changes there were. We’ll return to our usual Tip next week. 🙂
The Last 12 Months
In the last 12 months, I have published:
- The OWASP Top 10 Series
- Security Audits Top 10 Series
- 33 Security Tips
- 11 In Depth Articles
- Walked through my “Th1nk Lik3 a H4cker” talk in 2 parts (1, 2).
The OWASP Top 10 series sounded like a great idea when I decided to do it, and it was good to cover each of the points, but it didn’t really fit with the feel of Securing Laravel. It’s mostly broad concepts now, which are broken up into a number of sub topics and smaller vulnerabilities - many of which we’d covered already.
My Security Audits Top 10 series, on the other hand, was a huge success in my opinion. It felt really good to be working through my list of the security issues that most commonly occur in Laravel apps and providing practical tips and teaching on those specific topics. Some of which we’d covered before, and I was able to tie in related topics in those spots.
The Security Tips covered a very wide range of topics, which is the whole point, and I hope you were able to learn a bunch of things throughout the year.
My In Depth posts were the monthly features, and I’m really proud of what we covered these last 12 months. Let’s take a look through the list:
- OWASP In Depth: A01:2021 - Broken Access Control
We started off by covering the top OWASP Top 10 topic, and dived into subtopics like the principal of least privilege, Insecure Direct Object References (IDORs), Missing Authorisation, etc. There is just so much to this topic - it’s at the top of the OWASP Top 10 for a reason! - OWASP In Depth: A05:2021 – Security Misconfiguration
Another chunky OWASP topic, looking at securing hardening, unnecessary features, default accounts, error handling, security features, security headers, etc… And let’s not forget OWASP’s parting shot: “Without a concerted, repeatable application security configuration process, systems are at a higher risk.” 😱 - OWASP In Depth: A08:2021 – Software and Data Integrity Failures
The third OWASP In Depth was likewise quite chunky, and covered securing infrastructure, dependencies, and objects… Noticing the pattern here with these OWASP posts? - In Depth: "Password Generator" Security Audit
I really loved doing this one - we worked through a security audit on Steve McDougall’s password generator tutorial, looking at why his implementation was insecure and how we could fix it. I want to do more articles like this one, as they contain real practical tips and experience. - In Depth: Stealing Password Tokens with Forwarded Host Poisoning
This was another fun one! I covered a known Password Reset Vulnerability in Laravel apps that have been misconfigured, and then talked about my doomed attempt to fix it. We talk about spoofing hosts, stealing tokens, and why this stuff is so difficult. - In Depth: Securing Randomness Without Breaking Things
The second in my unintentional series of failed attempts to fix things… I talk about my attempt to upgrade the randomness helpers in Laravel to proper cryptographically secure implementations, and why it had to be rolled back. This is a great one if you’re interested in cryptography, randomness, or even backwards compatibility. - In Depth: Mass-Assignment Vulnerabilities
It was time for the humble Mass-Assignment vulnerability to be explored in depth. We walk through a vulnerability I found during a security audit, why`$fillable`is fundamentally flawed, and how I avoid these in my apps. - In Depth: What Are Insecure Functions?
This week we attempted to resolve the question of what are Insecure Functions, which is a fascinating rabbit hole to dive into. This post covers a variety of topics around insecure functions, and insecurity in general. - In Depth: Storing Environment Variables Safely
The most common issue I find during security audits are folks not storing their secrets/credentials/tokens/API keys correctly. So we dove deep into the topic, to explore the different options for keeping secrets safe. - In Depth: "Th1nk Lik3 a H4cker" Walkthrough (part 1)
Part 1 of the walkthrough of my “Th1nk Lik3 a H4cker” talk from Laracon EU and US. It was so much fun to explore each of the challenges, explaining my thinking and aims at each step, so even if you couldn’t attend my talk, you could learn from it. - In Depth: "Th1nk Lik3 a H4cker" Walkthrough (part 2)
Part 2 of the walkthrough, since I only managed to fit half of it into the first email. This one includes my fun cookie hijack trick I added for Laracon US!
In almost every one of the above articles, I was hitting the Substack email length limit. This is the point at which mail clients, such as Gmail, will truncate the email. So I work hard to keep it under the limit…
Also, something I started 12 months ago was to include a “Looking to learn more?” section in each email, linking to my older emails. One Tip and one In Depth, working through chronologically from #12. My intention was to surface older emails with topics that are still relevant, so you can go back and learn about them or refresh your memories.
The Most Popular
According to Substack, these are the most popular posts from the past 12 months:
- Security Tip: Restricting Local File Access
This was a simple tip covering handling local file loading securely. It surprised me at how popular this one was (and still is)! - Security Tip: Bypassing CSRF Protection with File Uploads
Another file upload one… I’m noticing an interesting pattern here. - In Depth: Storing Environment Variables Safely
It shouldn’t be a surprise the #1 issue I found during audits is a popular topic to learn about. - In Depth: "Th1nk Lik3 a H4cker" Walkthrough (part 1)
It’s great to see this style of post is so popular. - In Depth: Mass-Assignment Vulnerabilities
One of my favourites and something I feel passionate about, so it’s good to see it so popular.
The Schedule
If you love patterns like me, you may have noticed that I don’t send emails out on the same day and time each week. When I started this, I decided to send out each email exactly 1 week, 1 day, and 1 hour after the previous email. So if one goes out Monday 10am, the next would be Tuesday the week after at 11am. I still really love this quirk and am still sticking to it. No one has ever mentioned it to me though… ¯\_(ツ)_/¯
Changing the Name
Back in May this year, I changed the name from Laravel Security In Depth to Securing Laravel and shifted it over to a custom domain, securinglaravel.com. I wrote an email about why I made the change at the time, so check that out if you’re interested in the details. 🙂
A few months after I can happily report that I am incredibly happy with the new name and domain. It works really nicely with the feel of the list, and the domain is easier to remember and type. So I’m counting this as a big win.
The one downside of changing the name is, Laravel Security In Depth had a fantastic acronym: LSID. Securing Laravel just has SL, which is far less obvious. 😔
The Subscribers
In terms of the growth of Securing Laravel, it’s been pretty consistent from the start. We had 1,172 subscribers 12 months ago, and that number has more than doubled to 2,521 at the time of writing this. I’m hoping we can get that to 4,000 or even 5,000 next year! 🤞
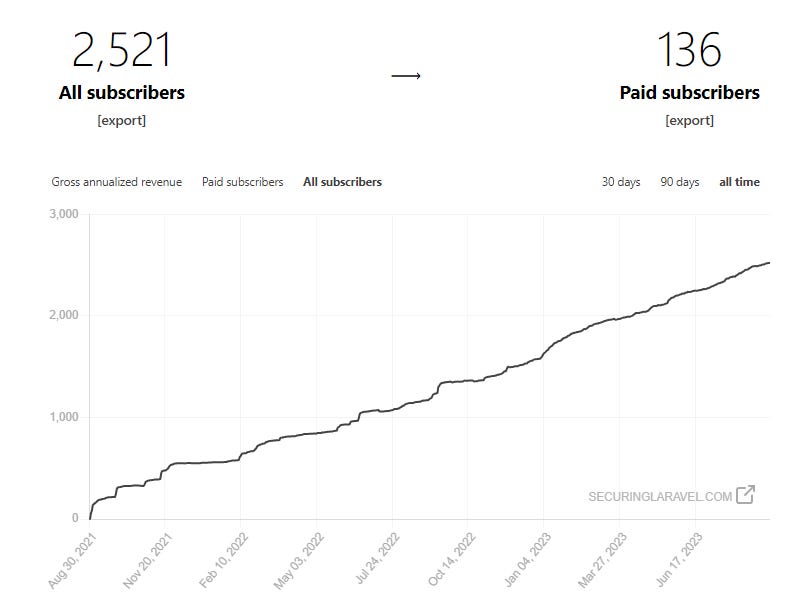
It is also really encouraging to see so many paid subscribers have signed up and continue to renew each month. I truly appreciate those who are able to support Securing Laravel financially, and allow me to dedicate the time each week to writing my emails.
When I started, this was definitely a labour of love that I was working on in my free time, with the subscription fees being nice bonuses to buy me a drink while I worked out of the house. But now, while it’s still definitely something I love doing each week, it has reached the point where it’s actually properly paying for my time! As a self-employed consultant, this is a huge win and means this can be counted as work time. I am so appreciative of my paid subscribers for allowing me to do this each week. 🥰
Leaderboard
One of the things I love about Substack is their network, and the different methods they have to help you find subscribers. One of their cooler ideas is a referrer leaderboard, where you can get complimentary paid subscriptions for referring new subscribers.
As of today, Ash Allen is doing pretty well at 7 subscribers:
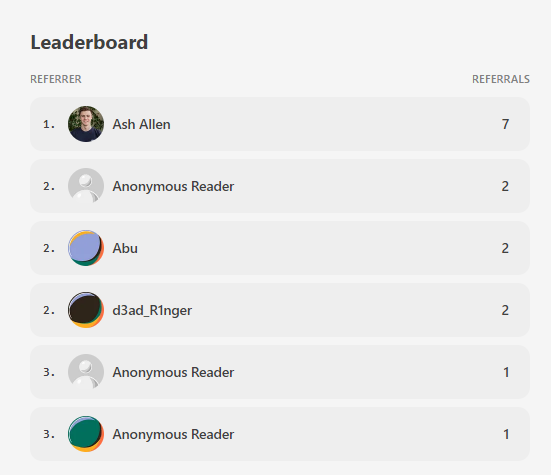
So if you’re keen to read the paid articles, why not refer some folks. 🙂
What’s Next?
I shall keep writing my Tips and In Depths!
I talked about doing a “debunking PHP myths” series a while ago, and I’d love to explore that idea further, although the arguments against PHP are consistently baseless to the point where there is nothing to actually debunk. It’s just all generic statements like “PHP is insecure”, without a why. So I don’t have much to work off on this one yet…
My next big plan is to start laying the groundwork for doing security reviews of popular Laravel packages. I’d love to work through the popular Laravel packages and help them upgrade their security, while teaching all of you about the security considerations they are dealing with. Packages have very interesting security implications outside of your normal application level risks.
I need to approach this carefully though, as there are matters of disclosure to consider, plus I need to find some good packages to start with. I am thinking this will become part of paid subscriber perks - suggesting and voting on packages to audit.
On the subject of paid subscribers, I’ve opened up a 25% discount for the next week to celebrate the 2-year anniversary. So if you’ve been thinking of subscribing, or want to support my security work within the Laravel community, now is a great time to upgrade:
Ok, that’s more than enough from me!
Now I’d love to throw it over to you: What do YOU think about Securing Laravel? What do you love? What should I change? How can I improve it?
Leave a comment below, or send me an email!
I put this poll up last year, so it’s only fitting I run it again this year:
Finally, thank you all once again for your support of Securing Laravel. It means the world to me, and I appreciate all of you. I would not be doing this if it wasn’t for you. 🥰
Thank you.
Stephen






