
In Depth
In Depth: Stealing Password Tokens with Forwarded Host Poisoning
[InDepth#13] User input comes in many different forms, and sometimes your app will believe whatever your users tell it... especially if it's in a header!
Monthly deep dive into Laravel security concepts through code examples, practical security knowledge, hacking techniques, and interactive challenges, covering the essential topics you need to know to keep your apps secure.

In Depth
[InDepth#13] User input comes in many different forms, and sometimes your app will believe whatever your users tell it... especially if it's in a header!
In Depth
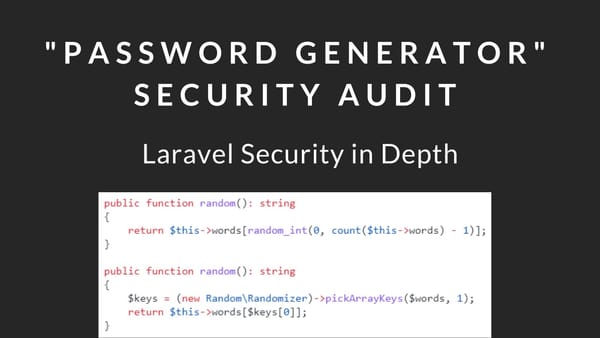
[InDepth#12] In November 2022, Steve McDougall published a tutorial called "Creating a Password Generator"... we're going to audit his code!

OWASP Top 10
It's a three-in-one for the third last entry into our OWASP Top 10 series!

OWASP Top 10
From Insecure Design last week to Insecure Configuration this week!

OWASP Top 10
Let's dive into the first risk in the OWASP Top 10...
In Depth
[InDepth#11] Also known as hide-and-seek, and security through obscurity!

In Depth
[InDepth#10] One time codes, magic links, and more...
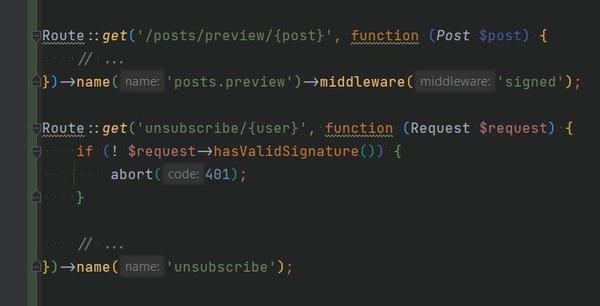
In Depth
[InDepth#9] One of the many awesome and completely underrated Laravel security features.
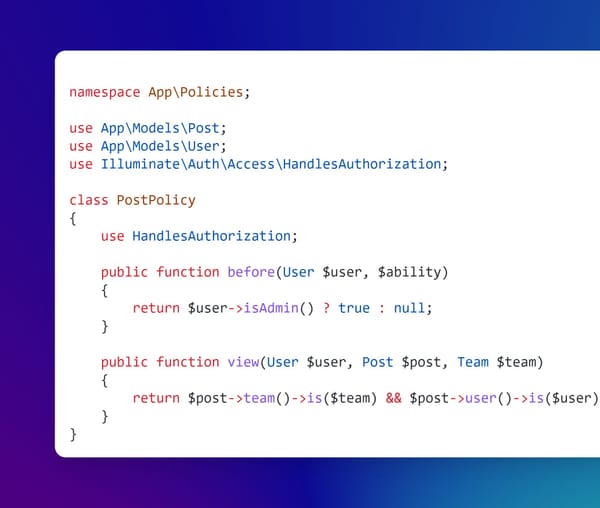
In Depth
[InDepth#8] Policy Objects are incredibly powerful. Use them.

Newsletter
[InDepth#7] CSPs are an incredibly powerful security feature built into the browser.
In Depth
[InDepth#6] You can use response timing to infer important information.
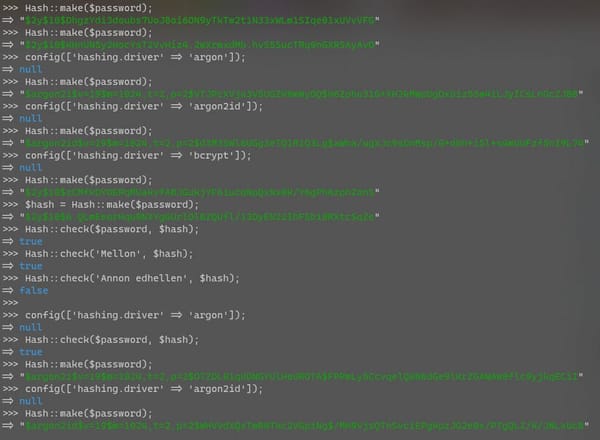
In Depth
[InDepth#5] It sounds easy to rehash passwords, but is it really that easy?