
In Depth
In Depth: Graceful Encryption Key Rotation
[In Depth #25] Laravel makes effective use of encryption for security purposes, but what happens if your encryption key needs to be rotated? Let's see how Laravel 11 handles it...
Monthly deep dive into Laravel security concepts through code examples, practical security knowledge, hacking techniques, and interactive challenges, covering the essential topics you need to know to keep your apps secure.

In Depth
[In Depth #25] Laravel makes effective use of encryption for security purposes, but what happens if your encryption key needs to be rotated? Let's see how Laravel 11 handles it...

In Depth
[InDepth#24] It's time to answer the question: how do you build user registration and authentication without an enumeration vector?

Newsletter
[InDepth#23] Staging sites usually contain buggy code, debugging tools, and lower security than production, while also being a gateway into your environment and sometimes even contain customer data...
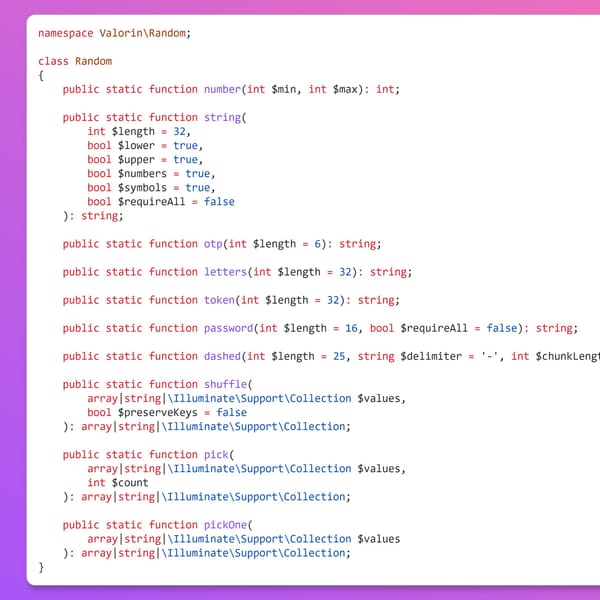
In Depth
[InDepth#22] Random generates cryptographically secure random values in a range of different formats through a simple helper package for PHP.

In Depth
[InDepth#21] I've had this question many times, so let me take you through the steps I follow when provisioning and securing apps on Forge.
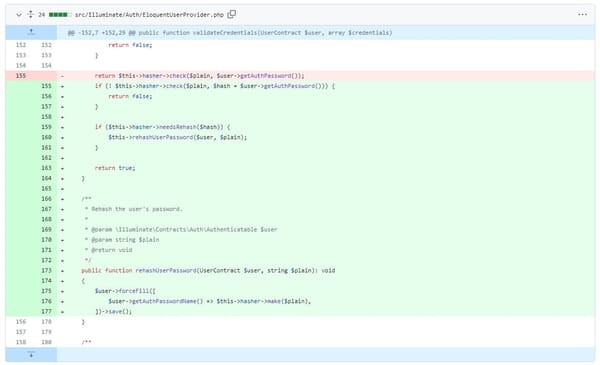
In Depth
[InDepth#20] It turns out Laravel was missing an important piece of it's Authentication system: password rehashing! Let's add that in and learn how the authentication system works in the process.
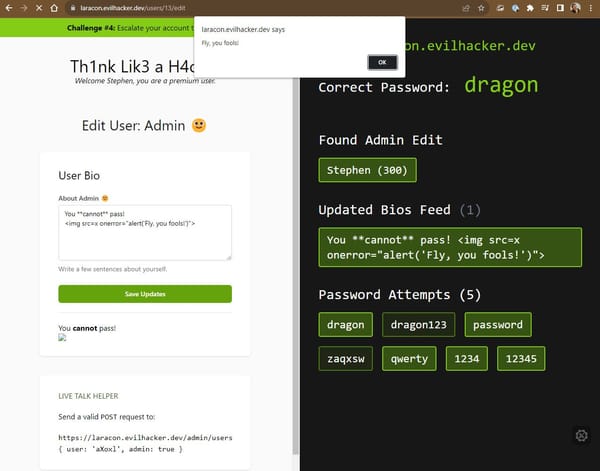
Newsletter
[InDepth#19] It's time to finish up the "Th1nk Lik3 a H4cker" walkthrough, looking at the rest of the challenges and the final hack from Laracon US!
In Depth
[InDepth#18] Let's take a walk through the first half of my "Th1nk Lik3 a H4cker" talk from Laracon EU & US. We'll explore the vulnerabilities behind each challenge and what I was trying to teach.

In Depth
[InDepth#17] Let's dive deep into the wonderful world of storing environment variables safely, looking at the different options Laravel supports and some "industry best practices".

In Depth
[InDepth#16] According to random folks on the internet (i.e. social media), "insecure functions" are a wide and varied concept. Let's take a look at the common themes across the different ideas...

In Depth
[InDepth#15] There is a false confidence about mass-assignment vulnerabilities that hides how easy it is for them to occur and be exploited...

Newsletter
[InDepth#14] Cryptographically secure randomness is important, but so is backwards compatibility...