
Security Tips
Security Tip: Don't Generate Your Own Passwords!
[Tip #113] "Don't Roll Your Own Crypto" applies to password generators too! It's way too easy to unknowingly lower your entropy by trying to be clever... 😱

Security Tips
[Tip #113] "Don't Roll Your Own Crypto" applies to password generators too! It's way too easy to unknowingly lower your entropy by trying to be clever... 😱

Security Tips
[Tip #106] Laravel 12 gives us the ability to reject passwords longer than 72 bytes for bcrypt, but you need to turn it on manually. Oh, and don't forget to add a validation rule, or you'll be throwing suspicious 500 server errors! 😱

Security Tips
[Tip #103] It's story time! Let's look at the SHA-3 competition as a reminder that crypto is hard... 😱

In Depth
[In Depth #32] Let's explore 5 different "Authentication Fails" that I've come across, as a reminder for why it's so important to get authentication right.

In Depth
[In Depth #31] Here are the Top 10 security issues I've found during my security audits, highlighting the areas we as a community need to improve our security.

Security Tips
[Tip #94] Just like we can detect insecure functions with Pest, we can use PHPStan extensions to find and disallow insecure functions!

Security Tips
[Tip #93] Test suites aren't just for raw code expectations, it turns out you can also use them to encourage secure coding practices!

Security Tips
[Tip #87] MD5 is like a cockroach - it's persistent and pops up everywhere, but one thing is very clear: you need to stop using it (and SHA-1 too)!

In Depth
[In Depth #25] Laravel makes effective use of encryption for security purposes, but what happens if your encryption key needs to be rotated? Let's see how Laravel 11 handles it...
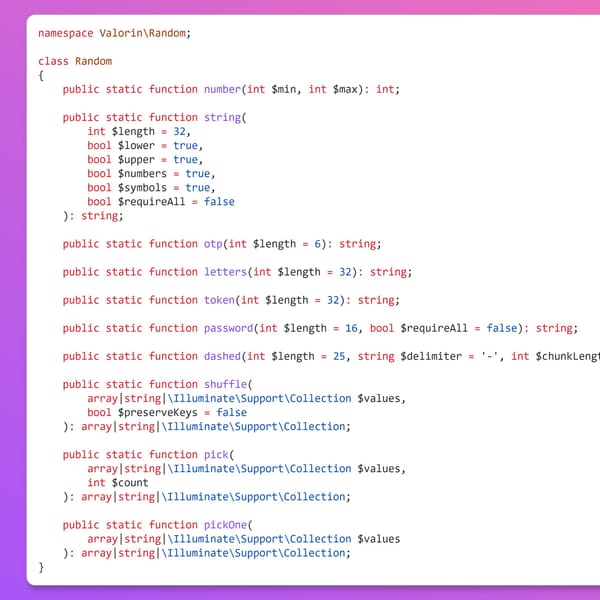
In Depth
[InDepth#22] Random generates cryptographically secure random values in a range of different formats through a simple helper package for PHP.

Security Tips
[Tip#66] For those situations where you need to generate a repeatable hash or signature, reach for HMAC, rather than MD5 or SHA1.

Security Tips
[Tip#56] It may be tempting to compare keys/sensitive strings using `===`, or even `==`, but that opens you up to timing attacks! You should be using a timing attack safe string comparison function...