Security Tip: What Is An HttpOnly Cookie?
[Tip #86] Cookies come in many shapes and sizes, and with multiple attributes just to confuse you... Have you ever wondered what the humble HttpOnly attribute actually does?

Cookies are a fundamental part of the internet, especially for PHP and Laravel developers like ourselves. Without them, we wouldn't have authenticated sessions that persist across page refreshes, or remember me tokens to avoid logging in every day. (We also wouldn't have Cross-Site Request Forgery (CSRF) tokens, or a need for them, but that's another topic!)
Since cookies are so fundamental to what we do and Laravel basically handles them for us, it's easy to completely overlook how they work and the different options available. So with this in mind, let's take a look at one of the features, or attributes, of cookies: HttpOnly.
The HttpOnly cookie attribute instructs the browser to prevent javascript from accessing that cookie. The cookie will still be sent to the server, but the javascript has no way to access it, preventing XSS attacks (and 3rd party scripts) from stealing those cookies.
This is especially important to Authentication and Remember Me cookies, as these values allow anyone who possesses them to be logged in as the user. If an XSS attack can steal a user's Authentication cookie, they'll get access to the user's account.
If we take a look in Laravel's default config/session.php file, we'll see this option near the bottom:
/*
|--------------------------------------------------------------------------
| HTTP Access Only
|--------------------------------------------------------------------------
|
| Setting this value to true will prevent JavaScript from accessing the
| value of the cookie and the cookie will only be accessible through
| the HTTP protocol. It's unlikely you should disable this option.
|
*/
'http_only' => env('SESSION_HTTP_ONLY', true),Laravel defaults to HttpOnly on its session cookies, and unless you're doing something very specific (and have other controls in place), you'll want to keep this enabled.
*_session). The 'remember me' cookie (remember_web_*), and any custom cookies you create will inherit the Laravel (and Symfony) default of HttpOnly=true. You'll need to override this when configuring your cookie to disable it.What about the XSRF-TOKEN Cookie?
I see this question a lot, so I wanted to address it quickly here. If we take a look at a set of cookies from a standard Laravel app:
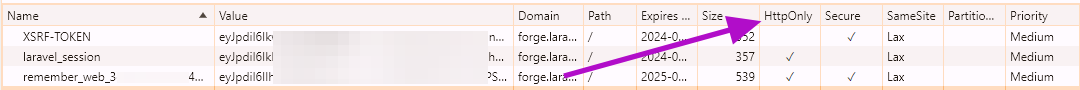
You'll notice that while both larave_session and remember_web_* have HttpOnly set, the XSRF-TOKEN cookie is left without HttpOnly, allowing javascript to access it directly. This is by-design.
The XSRF-TOKEN cookie is a method of providing your CSRF token to javascript toolkits, so they can automatically detect and include it in any requests they make back to your site - avoiding the need for you to manually handle it in tour code yourself.
If you found this security tip useful? 👍
Subscribe now to get weekly Security Tips straight to your inbox, filled with practical, actionable advice to help you build safer apps.
Want to learn more? 🤓
Upgrade to a Premium Subscription for exclusive monthly In Depth articles, or support my work with a one-off tip! Your support directly funds my security work in the Laravel community. 🥰
Need a second set of eyes on your code?
Book in a Laravel Security Audit and Penetration Test today! I also offer budget-friendly Security Reviews too.
Finally, connect with me on Bluesky, or other socials, and check out Practical Laravel Security, my interactive course designed to boost your Laravel security skills.





