Security Tip: The Cookie ‘Secure’ Flag
[Tip #5] Don't forget to configure your cookies for to only work over HTTPS.

There are multiple flags that can be set on browser cookies, but the one we’re talking about today is the Secure flag. This flag instructs the browser to only accept the cookie if the connection is considered secure, i.e. over HTTPS. If you visit the site over HTTP, the browser will not send or receive any cookies with the flag set.
This is important for security as HTTP requests are not encrypted. If someone can monitor the connection between you and the server, they can read all of the contents of the request and response. This includes your cookies, and if these include a session token, they can hijack your account.
This attack was exploited by a Firefox extension called Firesheep back in 2010, which monitored the network you were connected to and stole any usable session cookies to popular social media sites. When it first came out, this plugin was very popular on free public wifi, for obvious reasons!
This video provides a great demo of it in action:
The Solution
The solution is simple, set the session.secure config value to be true on production and use https:// exclusively. This will fully protect your cookies from this attack, as they will never be sent over an unencrypted connection.
Laravel provides an env var for it by default, SESSION_SECURE_COOKIE, and in v11+ it should default to true on HTTPS connections:
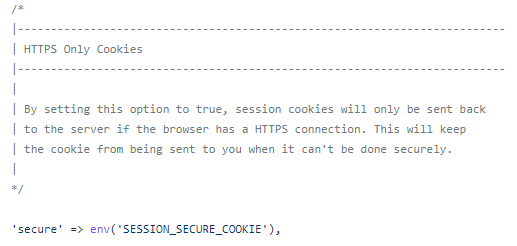
On older versions, or to ensure it's properly set, I recommend you update the ./config/session.php file in your apps to default to true, like this:
'secure' => env('SESSION_SECURE_COOKIE', true),And then add it into your .env.example file as a commented out option for local dev overrides:
SESSION_DRIVER=file
SESSION_LIFETIME=120
#SESSION_SECURE_COOKIE=trueThis ensures that your deployed apps will have the secure flag set by default, while also providing your developers with a simple way to disable the flag if they use HTTP for local development.
It’s the best of both words and will keep your cookies secure.
Found this security tip helpful? Don't forget to subscribe to receive new Security Tips each week, and upgrade to a premium subscription to receive monthly In Depth articles, or toss a coin in the tip jar.
Reach out if you're looking for a Laravel Security Audit and Penetration Test or a budget-friendly Security Review, and find me on the various socials through Pinkary. Finally, don't forget to check out Practical Laravel Security, my interactive security course.





