Security Tip: Protect Your .env File!
[Tip#62] Search engines like to snoop on all of your files, so be careful what you leave lying around.

I stumbled upon an interesting tweet this morning from @AshboDev on Twitter:
It sparked some interesting questions and recommendations, which we’ll get to shortly, as well as this reply/quote from @akshitarora0907 that demonstrates the issue nicely:
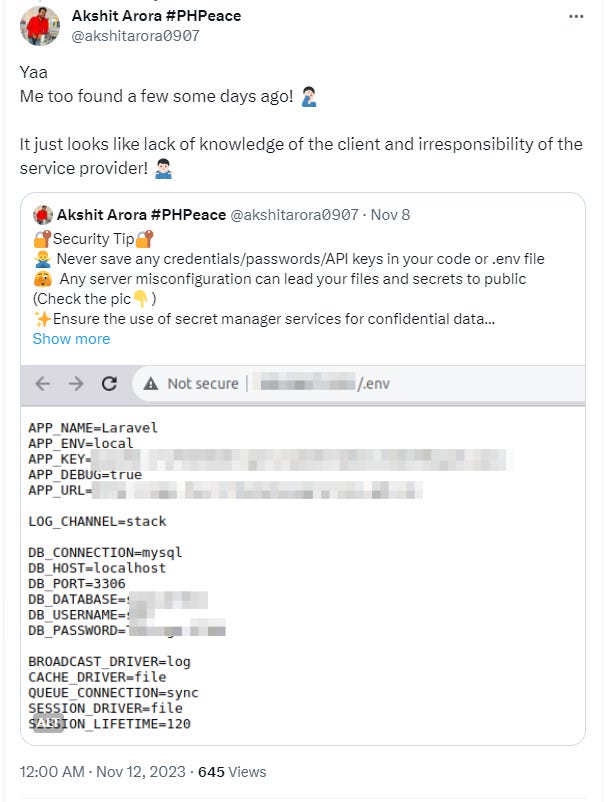
It’s very clearly an issue on some sites, one which you can easily exploit using a technique called Google Dorking, which makes it trivial to find exposed .env files.
I just performed a quick dork, which revealed 20+ sites on the first page of results - exactly what I expected to find. These are just the ones Google is aware of - there would be significantly more that haven’t been detected yet, which you could find manually or over time as Google picks them up.
Many of these will contain APP encryption keys, database credentials, API keys, etc, many of which are usable for further exploitation of the app or the associated accounts. For example, finding Stripe keys would allow access to the payment systems…
How Does This Happen?
By design, Laravel keeps all but the essential files outside the public/ directory, and you’re supposed to configure your apps so only the public/ is accessible on the web. This means that files like .env aren’t accessible at all, and you’re safe from this issue entirely.
However, some environments don’t support putting files outside the web root - shared hosting is a common scenario where this happens, or if you’re managing your own server and you’re unaware of the purpose of the public/ directory. In these instances, your files outside public/ are web accessible and sensitive information, such as your .env can be exposed.
It’s not just the .env which is an issue, but any other file in your directory - such as auth.json, or cache files, config files, etc… the options are plentiful.
How Do You Prevent It?
- Install your apps so
public/is the only web accessible directory.
This is super important, so always try this first! If you use a service like Laravel Forge, this is done automatically for you. - Add specific rules into Nginx/Apache to block accessing your sensitive files.
Laravel forge does this as an extra layer of protection by blanket blocking all`.*`files. This also blocks access to.git, which is another huge security risk.location ~ /.(?!well-known).* {
deny all;
} - Set environment variables in the server environment or use XYZ secure config storage solution.
I’ve included these as they are legitimate solutions, but only at #3 as you only really want to mess around with these options when you’re managing a large app across multiple servers. It adds a lot of complexity you really don’t want to deal with on a simple app, and I’d personally recommend just sticking with a`.env`file and installing Laravel properly.
(If you want me to go into more detail, or you disagree, please jump in the comments and I’ll happily continue the conversation!)
We’ll finish up here, since this is a security Tip, not an In Depth, but the key takeaway is to install and configure your Laravel apps so the sensitive files are not web accessible.
If you’re not comfortable configuring your site securely and getting the web config right, then I highly recommend checking out a service like Laravel Forge, which will handle it all for you.





