Security Tip: 2FA Isn't Just For Logins!
[Tip #118] Account passwords are easy to compromise, so why are you relying on them to verify users within your app? If your users log in with a 2FA Token, then they should be able to prove it before performing other sensitive activities too.

Last time we took an In Depth look at Setting Up Two-Factor Authentication, and today I wanted to remind you that MFA isn't just for your login flow! If you haven't yet read that article, do check it out. I'm incredibly proud of how much we covered!
Any time you want to authenticate that a legitimate user is performing a specific action, you can use one of your authentication factors. If you have multiple factors in your login flow, that gives you multiple options to use within the application too - not just your password!
Consider the humble Change Password form:
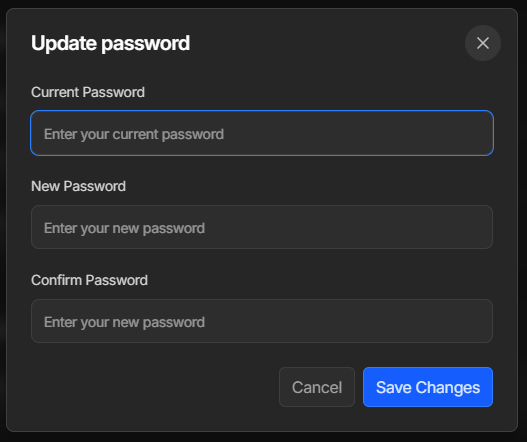
Right at the top, we're asked to confirm our Current Password. This is to check that we are the user of this account, and is designed to prevent an attacker from setting their own password during attacks like session hijacks or forgotten logouts on shared computers.
We're all so accustomed to this pattern that we don't even think twice. Laravel even provides a Password Confirmation option, in the form of the password.confirm middleware. This gives us a trivial way to protect specific routes with an additional password confirmation challenge.
We could stop here, but this pattern could very easily be implemented for any of your other authentication factors too!
Consider the confirmation we implemented when disabling 2FA in our 2FA implementation:
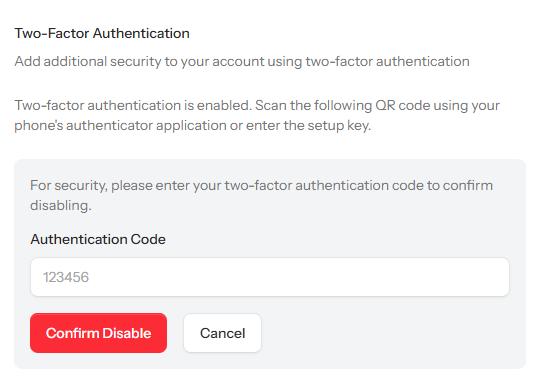
In order to disable 2FA, the user must first confirm that they have access to the existing 2FA token! This is done for the same reason you require the current password during a password change.
But why stop there?
You could ask the user to confirm their 2FA Token before all sorts of sensitive operations, such as:
- Viewing and/or changing billing details
- Changing account email address
- Accessing admin tools
- Accessing tenant configuration
- User impersonation
- Viewing PII or PHI
- and many more...
Account passwords are easy to compromise, so why are you relying on them to verify users within your app? If your users log in with a 2FA Token, then they should be able to prove it before performing other sensitive activities too.
So don't just treat your 2FA as something that only happens during the login process, keep using it as a form of authentication!
Want to see your brand here?
If you found this security tip useful? 👍
Subscribe now to get weekly Security Tips straight to your inbox, filled with practical, actionable advice to help you build safer apps.
Want to learn more? 🤓
Upgrade to a Premium Subscription for exclusive monthly In Depth articles, or support my work with a one-off tip or recurring Sponsorship! Your support directly funds my security work in the Laravel community. 🥰
Need a second set of eyes on your code?
Book in a Laravel Security Audit and Penetration Test today! I also offer budget-friendly Security Reviews too.
Finally, connect with me on Bluesky, or other socials, and check out Practical Laravel Security, my interactive course designed to boost your Laravel security skills.





