Security Tips
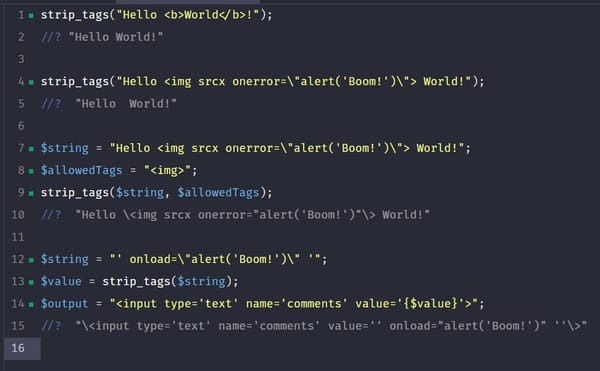
Security Tip: Is `strip_tags()` Secure?
[Tip#63] PHP includes a some really handy security-focused functions, but you need to know how to use them correctly, or you risk leaving a significant vulnerability waiting to be exploited! 😱

Security Tips
[Tip#63] PHP includes a some really handy security-focused functions, but you need to know how to use them correctly, or you risk leaving a significant vulnerability waiting to be exploited! 😱

In Depth
[InDepth#21] I've had this question many times, so let me take you through the steps I follow when provisioning and securing apps on Forge.

Security Tips
[Tip#62] Search engines like to snoop on all of your files, so be careful what you leave lying around.
Security Tips
[Tip#61] While it's tempting to throw everything into logs, keep in mind where your logs end up → plain text files, 3rd party collectors, passed around the development team, etc...

Security Tips
[Tip#60] Stack traces are essential for debugging complex (and even simple) issues, but there is a risk that something sensitive might be exposed within your trace... Let's ensure that doesn't happen!

Security Tips
[Tip#59] It may seem obvious, you'd be surprised just how often I come across websites where debug mode is enabled!
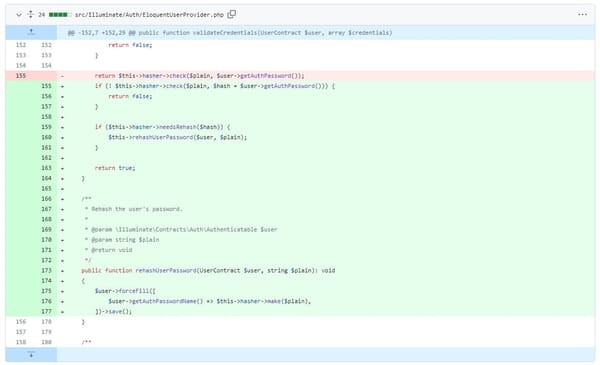
In Depth
[InDepth#20] It turns out Laravel was missing an important piece of it's Authentication system: password rehashing! Let's add that in and learn how the authentication system works in the process.

Security Tips
[Tip#58] It's time to upgrade your bcrypt rounds to 12 (or higher)!

Security Tips
[Tip#57] You've heard about SQL Injection and Cross-Site Scripting but what about another big injection avenue: Command Injection? It's less common but just as critical that you're aware of it...

Security Tips
[Tip#56] It may be tempting to compare keys/sensitive strings using `===`, or even `==`, but that opens you up to timing attacks! You should be using a timing attack safe string comparison function...

Birthday Retrospective
Thank you for subscribing and supporting Securing Laravel these past 2 years!
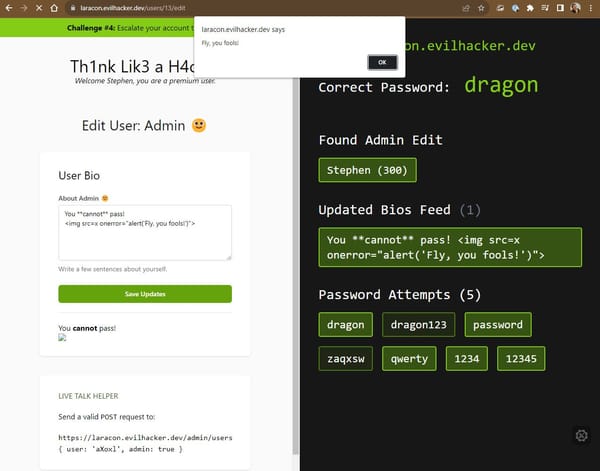
Newsletter
[InDepth#19] It's time to finish up the "Th1nk Lik3 a H4cker" walkthrough, looking at the rest of the challenges and the final hack from Laracon US!