Security Tips
Security Tip: Canary Tokens
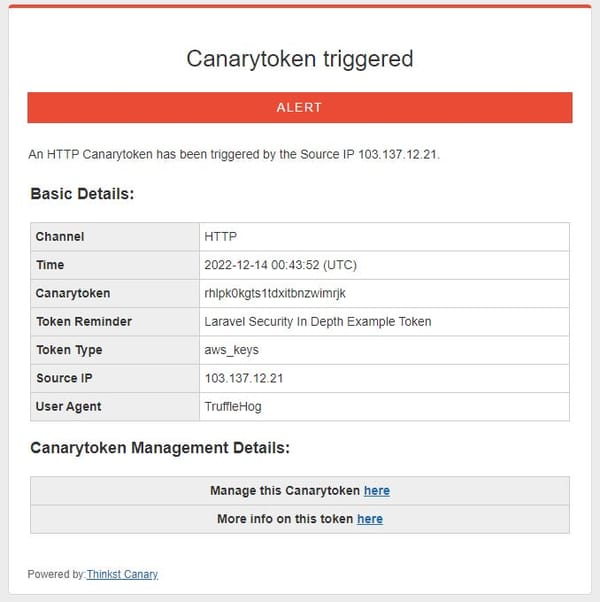
[Tip#31] These are my favourite simple security trick to let you know if someone is poking around in your stuff.

Security Tips
[Tip#31] These are my favourite simple security trick to let you know if someone is poking around in your stuff.

Security Tips
Our final entry in the OWASP Top 10 series - be aware of what your servers can access!

Security Tips
You do have logging enabled, right?

Newsletter
One last reminder about our Black Friday sale on Laravel Security in Depth subscriptions.

Newsletter
If you've been thinking of upgrading your Laravel Security in Depth subscription, now is the time!

OWASP Top 10
It's a three-in-one for the third last entry into our OWASP Top 10 series!

Newsletter
Get 25% off Laravel Security in Depth forever! 🥳

Security Tips
Don't get confused with authorisation, we're talking authENTICation this week.

Security Tips
Keep your stuff updated!!

OWASP Top 10
From Insecure Design last week to Insecure Configuration this week!

Security Tips
It's hard to build a secure system if the design is inherently insecure.

Security Tips
i.e. Cross-Site Scripting (XSS), SQL injection (SQLi), and Command Injection