Security Tip: Canary Tokens
[Tip#31] These are my favourite simple security trick to let you know if someone is poking around in your stuff.
Canary Tokens are a free service provided by Thinkst Canary that provide an “insanely easy-to-use honeypot solution that deploys in just 3 minutes.”
The way they work is incredibly simple:
- You generate a new token on their website.
- You put the token somewhere
- A hacker finds the token, interacts with it, and you get an alert!
(Most of the time, the hacker won’t even know they’ve triggered an alert!)
There are a lot of different tokens available to be generated, so you can usually find one that suits your use case.
The token types include:
- DNS / hostname
- AWS keys
- Windows Command
- Word Document
- QR Code
- MySQL Dump (this is great for your
'database'folder!) - URL Loaded
- URL Redirects
- Email address
Every time I set up a new Laravel app, I always generate a couple of tokens and scatter them around my repo and production server(s). The .env.example file is fantastic for storing Canary Tokens, because they’ll be stored in the repo and easily findable by anyone snooping around in your code. I’ve also got a few hiding on my laptop. 😉Let’s walk through a simple example: generating AWS keys.


Step Four: wait for someone to go snooping around!
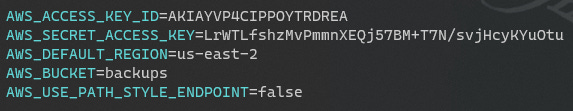
For this example, I’ve run TruffleHog on my codebase and it’s found some matches:
Found verified result 🐷🔑
Detector Type: AWS
Decoder Type: PLAIN
Raw result: AKIAYVP4CIPPOYTRDREA
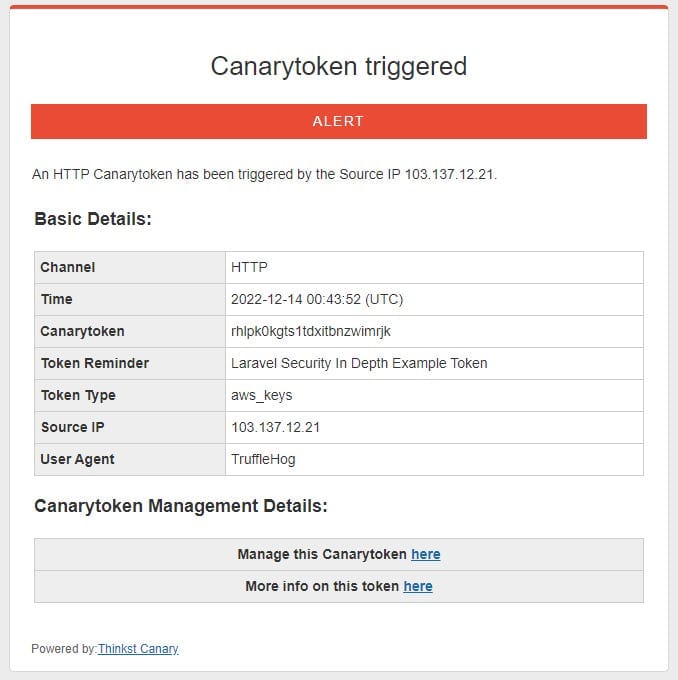
File: .env.exampleAnd I just received an email:
It really is that simple.
If you found this security tip useful, subscribe to get weekly Security Tips straight to your inbox. Upgrade to a premium subscription for exclusive monthly In Depth articles, or drop a coin in the tip jar to show your support.
When was the last time you had a penetration test? Book a Laravel Security Audit and Penetration Test, or a budget-friendly Security Review!
You can also connect with me on Bluesky, or other socials, and check out Practical Laravel Security, my interactive course designed to boost your Laravel security skills.





