In Depth: "Th1nk Lik3 a H4cker" Walkthrough (part 2)
[InDepth#19] It's time to finish up the "Th1nk Lik3 a H4cker" walkthrough, looking at the rest of the challenges and the final hack from Laracon US!
In Part 1 we looked at the first three challenges from my Laracon EU and US talk. To quickly recap each of the challenges:
- Challenge #1: Identify the correct password!
- Challenge #2: Escalate your account to premium!
- Challenge #3: Edit the Admin bio!
Now we’re up to Challenge #4, which can be found around 10:00 in the recording:
So let’s dive into it:
Challenge #4: Escalate your account to admin!
Here’s what the screen looks like at the start of Challenge #4:
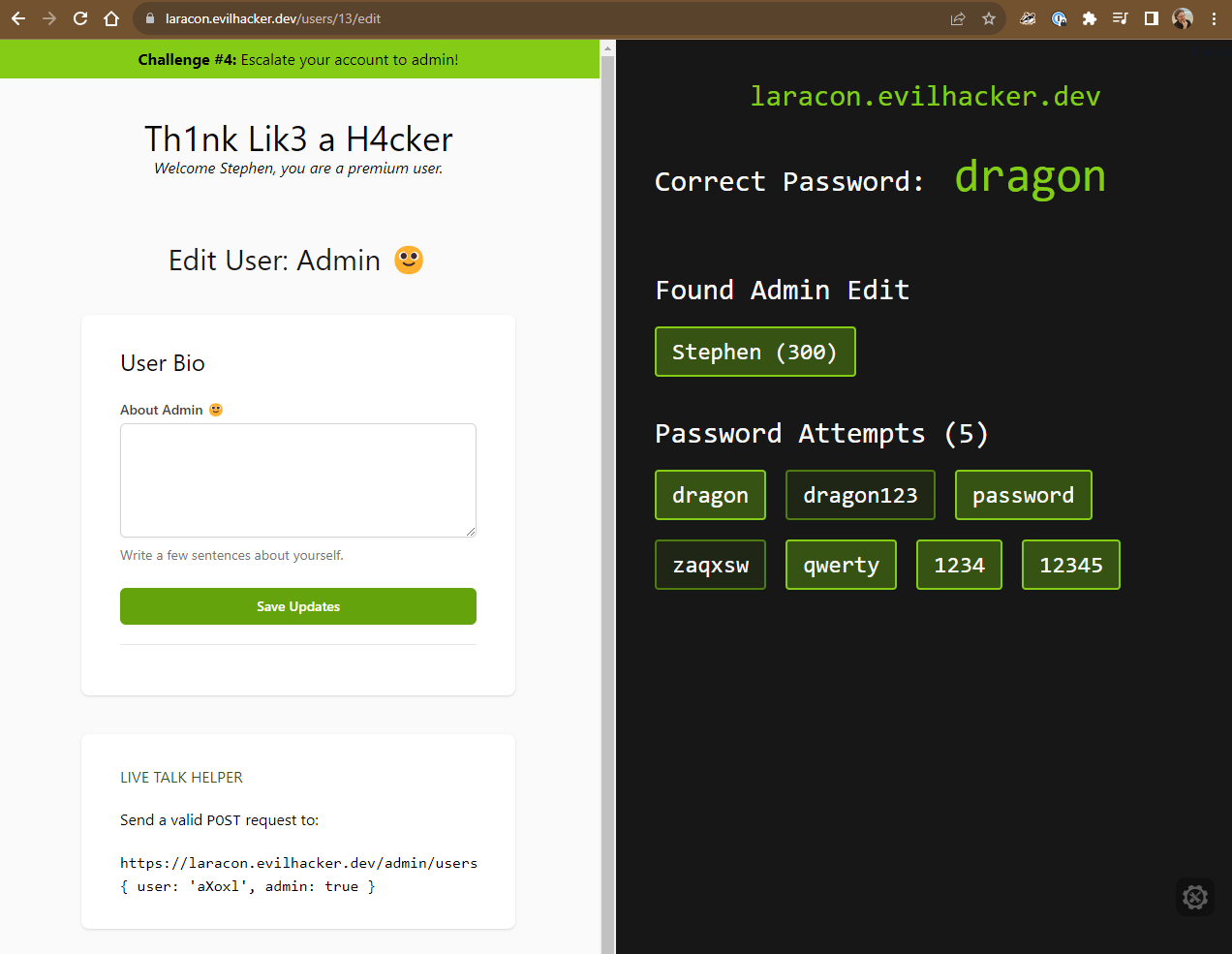
The challenge here is to escalate our account to an administrator account, which is known as a Privilege Escalation attack, or PrivEsc.
Unlike back in Challenge #2 when we could modify verification URL and perform the privilege escalation directly, we don’t have anything obvious here, so we’re going to go deeper to crack this one.
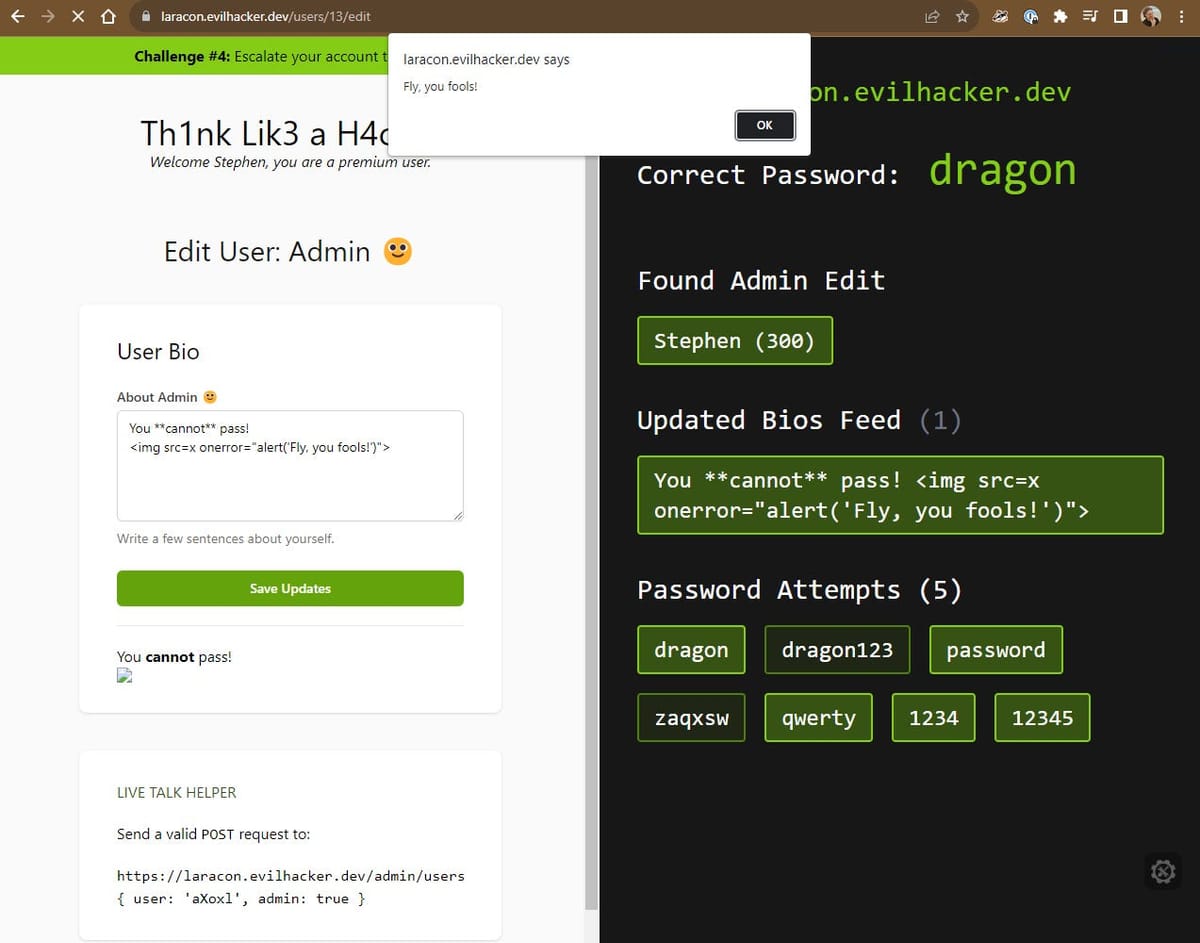
As we’ve talked about before, the first step is to see what we can modify and control. Looking for any vulnerable inputs or ways of interacting with the application. Our attack vector should be immediately obvious with that User Bio field that we can modify, so let’s see what it let’s us do…





