In Depth: "Th1nk Lik3 a H4cker" Walkthrough (part 1)
[InDepth#18] Let's take a walk through the first half of my "Th1nk Lik3 a H4cker" talk from Laracon EU & US. We'll explore the vulnerabilities behind each challenge and what I was trying to teach.
If you’ve seen one of my conference talks before, you’ll know that I love to do demos and practical talks, rather than talk off a bunch of slides. I find this the best medium for presenting security concepts, as it gives the audience a feel for the mentality of the hacker and how they approach exploiting each vulnerability.
When I started planning my Laracon EU talk, it was going to be my first in-person Laracon talk and I wanted to do something big and memorable, plus take advantage of having everyone in the same room as me. So I decided to go all-in and make the entire talk interactive!
I had one simple rule I had to follow: Everything must be hackable via a phone browser. I wanted the audience to be able to fully participate with their phones, rather than relying on laptops. This requirement somewhat limited and shaped the challenges - but not in a bad way - it just meant I needed to consider Javascript errors for the XSS challenge, and how to manipulate user input sent to the sever.
Thus, Th1nk Lik3 a H4cker1 was created:
Let’s dive into the fist challenge…
Challenge #1: Identify the correct password!
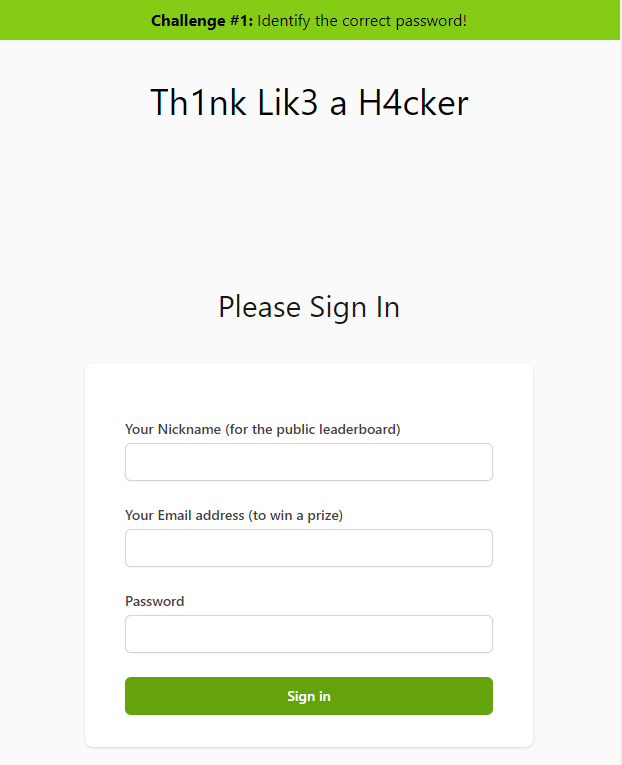
The apparent purpose of this challenge is a simple guessing game to identify the “correct password”, while in reality it’s actually here for multiple purposes (and getting the correct password has nothing to do with guesswork):





