In Depth #2: SQL Injection (SQLi)
Let's dive into SQL Injection, learn how it works, and what we can do with it.
Before we begin, I need you to promise that the skills I teach you will be used for good, not evil. If you’re here to do evil, stop reading now! 🫡
What is SQL Injection?
A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system. SQL injection attacks are a type of injection attack, in which SQL commands are injected into data-plane input in order to affect the execution of predefined SQL commands.
OWASP SQL Injection Overview
I like to think of SQL injection attacks modifying or hijacking a query for malicious purposes. They can happen any time the attacker is allowed to control some aspect of the query beyond what the developer is expecting.
There are two main types of SQL injection vulnerabilities:
In-Band / Classic SQL Injection
In-band or Classic SQLi vulnerabilities allow the attacker to directly see the results of the attacks. These typically take the form of:
- Bypassing or negating a query condition to produce different results than the query is supposed to produce. For example, this could be used to display all users instead of a specific subset of users.
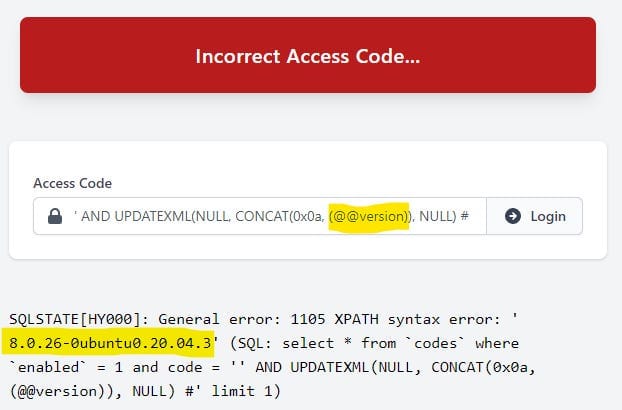
- Using
UNIONorJOINto include records from other tables in the output. This could be used to leak something like private messages from an unrelated query - maybe through an image gallery? You may need to get creative, but it’ll give you what you need. - Leaking information through error messages. Database error messages contain debugging information about what went wrong, which can include database, table, and column names, plus specific values and system variables. If you can control the query, you can manipulate what is included in the error message to leak information.





