In Depth: Pentesting Laravel part 4 - Reading Code Pays Off!
[In Depth #30] In the final part of the series, we finish our code searches and spend some time reading the code - which really pays off in terms of finding juicy vulnerabilities to exploit and report.

If you've missed any of the previous parts, go check those out first:
Part 1: Passive Scans
Part 2: Configs, Dependencies, and Routes
Part 3: Looking for "Interesting" Code
Part 4: Reading Code Pays Off!
To refresh your memories, last month we conducted a bunch of code searches, looking for interesting or smelly code. For me, this involves running a bunch of different regexes through PhpStorm, and eyeballing the results. Some of my searches are quite noisy and turn up a bunch of normal code that can be ignored, while others often have no results at all, but the end result is usually a bunch of suspicious bits of code that need further investigation. Digging into these will sometimes reveal weak or vulnerable code - which is exactly what I'm looking for!
So far, we've looked for:
- Remote Code Execution (RCE)
- Insecure Randomness
- Debuggging Statements
- Encoding and Files
- Open Redirects
- Cross-Site Scripting (XSS)
- Type Juggling
- SQL Injection (SQLi)
So, what's next?
Mass-Assignment & Uploads
Mass-Assignment is tricky to find because there are many different ways to send request data into models, so I have a couple of regexes I use for this. It also pays to check a couple of controllers and look for a pattern for how request data is passed around - as this can give you an idea for what to look for.
I've added detecting file uploads in here too, as it's all about handling user input - and unsafe file handling will usually be found in similar places to unsafe request handing (i.e. mass-assignments).
Here is my main search, it's not perfect and can be quite noisy, but it's helped on more than one occasion:
request.*\s*->\s*(all|collect)|->\s*(file|hasFile)\s*\(Running this against Chirped gives us this:
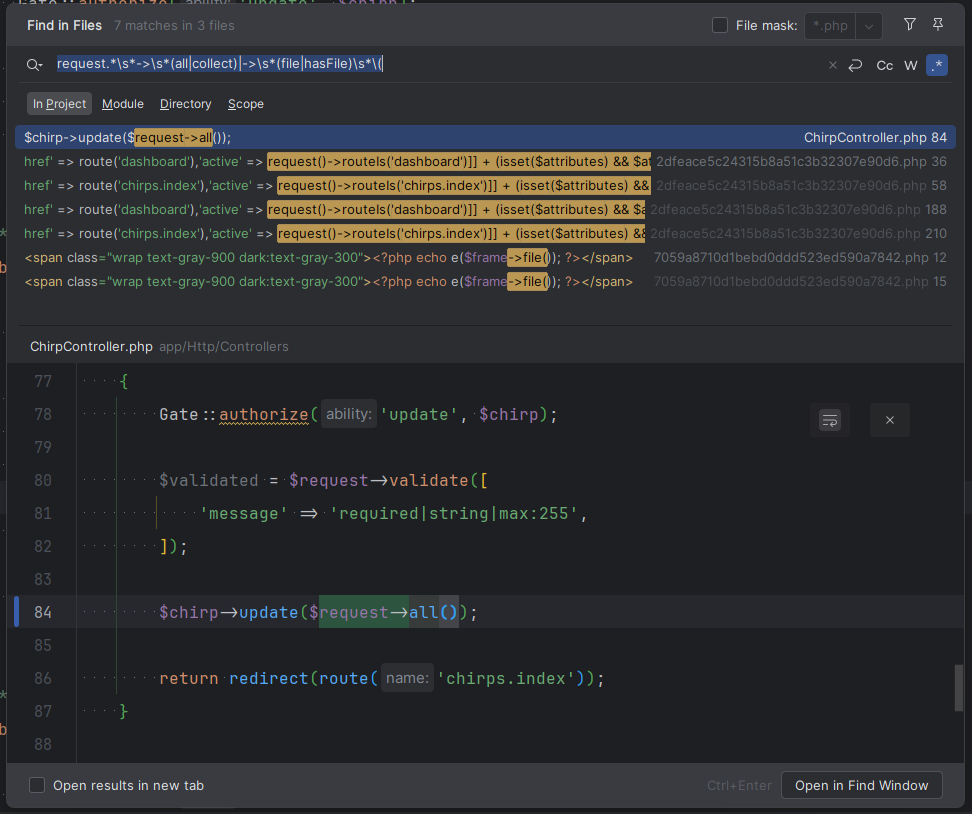
Ignoring the compiled Blade files, the first hit is quite promising.





